Overview
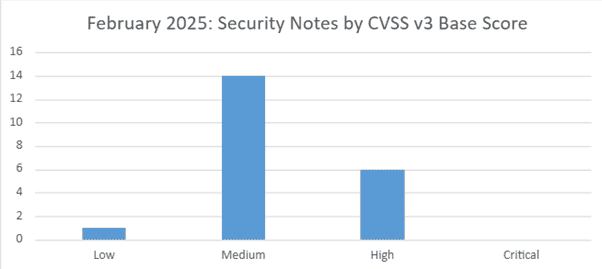
SAP’s security patch day for February 2025 has seen the release of 21 OSS SAP security notes. Six notes have been classified as high, fourteen as medium and one as low based on CVSS v3.0 Rating.
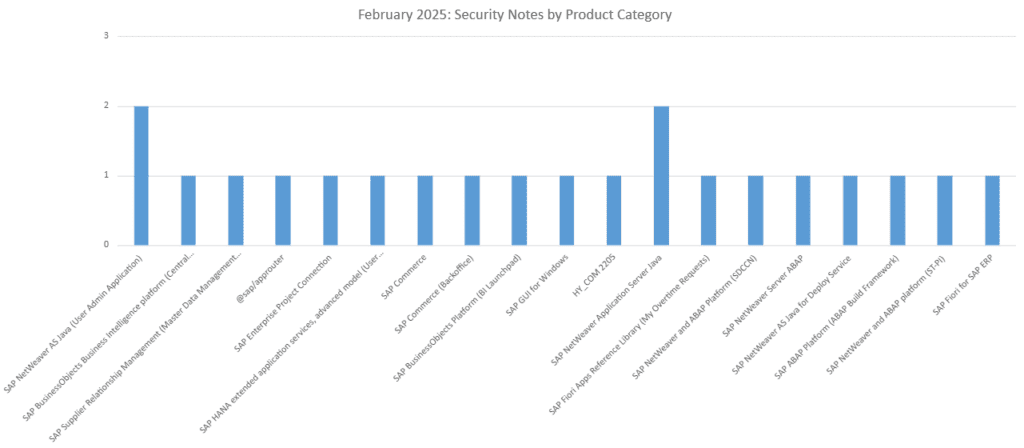
Two notes have been released for:
- SAP NetWeaver Application Server Java
- SAP NetWeaver AS Java (User Admin Application)
Single notes have been released for:
- SAP Supplier Relationship Management (Master Data Management Catalog)
- @sap/approuter
- SAP Enterprise Project Connection
- SAP HANA extended application services, advanced model (User Account and Authentication Services)
- SAP Commerce
- SAP Commerce (Backoffice)
- SAP BusinessObjects Platform (BI Launchpad)
- SAP GUI for Windows
- HY_COM 2205
- SAP Fiori Apps Reference Library (My Overtime Requests)
- SAP NetWeaver and ABAP Platform (SDCCN)
- SAP NetWeaver Server ABAP
- SAP NetWeaver AS Java for Deploy Service
- SAP ABAP Platform (ABAP Build Framework)
- SAP NetWeaver and ABAP platform (ST-PI)
- SAP Fiori for SAP ERP
Vulnerabilities: February 2025 Highlights
[CVE-2025-23187] Missing Authorisation Check in SAP NetWeaver and ABAP Platform (SDCCN) (SAP Note 3546470)
Along with CVE-2025-23189, this note addresses Missing Authorisation Checks in SDCCN. Due to vulnerabilities in an RFC-enabled function module, an unauthenticated attacker could generate technical meta-data. This leads to a low impact on integrity. There is no impact on confidentiality or availability.
[CVE-2025-23193] Information Disclosure vulnerability in SAP NetWeaver Application Server ABAP (SAP Note 3561264)
SAP NetWeaver Server ABAP allows an unauthenticated attacker to exploit a vulnerability that causes the server to respond differently based on the existence of a specified user, potentially revealing sensitive information. This issue does not enable data modification and has no impact on server availability.
[CVE-2025-23190] Missing Authorisation check in SAP NetWeaver and ABAP platform (ST-PI) (SAP Note 3547581)
Due to a missing authorisation check, an authenticated attacker could call a remote-enabled function module, allowing them to access data they would otherwise not have access to. The attacker can modify data or impact the availability of the system.
[CVE-2025-23191] Cache Poisoning through header manipulation vulnerability in SAP Fiori for SAP ERP (SAP Note 3426825)
Cached values belonging to the SAP OData endpoint in SAP Fiori for SAP ERP could be poisoned by modifying the Host header value in an HTTP GET request. An attacker could alter the values in the returned metadata redirecting them from the SAP server to a malicious link set by the attacker. Successful exploitation could have a low impact on the integrity of the application.
About this Review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.









